For those looking for a complete list of available techniques, including database-specific ones, the OWASP Project maintains a SQL Injection Prevention Cheat Sheet, which is a good place to learn more about the subject. Parameterized Queries. OWASP SQL Injection Prevention Cheat Sheet OWASP Query Parameterization Cheat Sheet OWASP Command Injection Article OWASP XML eXternal Entity (XXE) Reference Article ASVS: Output Encoding/Escaping Requirements (V6) OWASP Testing Guide: Chapter on SQL Injection Testing External CWE Entry 77 on Command Injection CWE Entry 89 on SQL Injection.
- Owasp Cheat Sheet Series
- Owasp Top 10 Cheat Sheet
- Sql Injection Examples
- Owasp Input Validation Cheat Sheet
Login page #5
- Login page with user name and password verification.
- MD5 Encryption used for password.
- Both user name and password field are prone to code injection.
Credentials for logging in normally
| User name | Password |
|---|---|
| harry | password |
SQL injection.
Executed SQL query when username is harry and password is password:
SELECT* FROMusers
FROMusersOwasp Cheat Sheet Series
WHEREname='harry'Owasp Top 10 Cheat Sheet
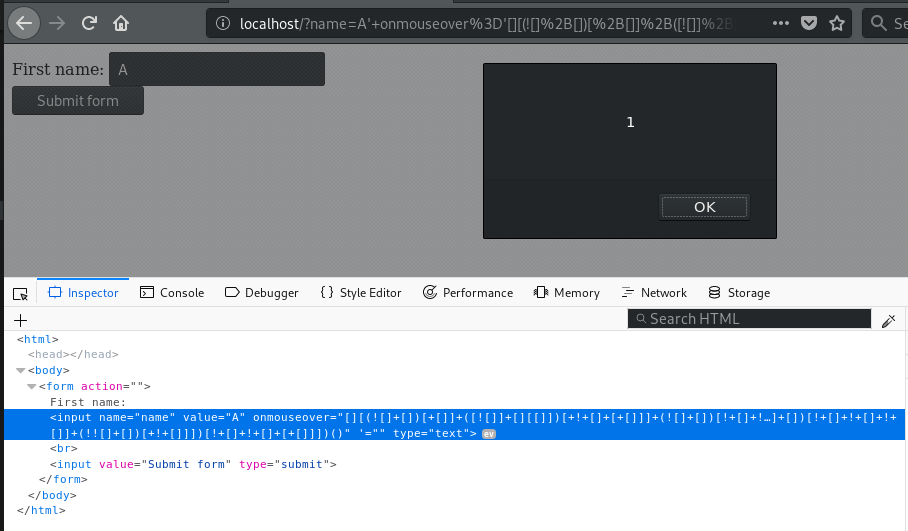 ANDpassword
ANDpasswordSql Injection Examples
='5f4dcc3b5aa765d61d8327deb882cf99'When a user enters a user name and password, a SQL query is created and executed to search on the database to verify them. However, the password is not stored as clear text on the database. They are encrypted with MD5 algorithm. The above query searches in the users table where name is harry and password is 5f4dcc3b5aa765d61d8327deb882cf99, which is the MD5 encrypted value of password. If matching entries are found, the user is authenticated.
In order to bypass this security mechanism, SQL code has to be injected on to the input fields. The code has to be injected in such a way that the SQL statement should generate a valid result upon execution. If the executed SQL query has errors in the syntax, it won't fetch a valid result. So filling in random SQL commands and submitting the form will not always result in successful authentication.
Owasp Input Validation Cheat Sheet
Cheat sheet
| User name | Password | SQL Query |
|---|---|---|
| harry | password | SELECT*FROMusersWHEREname='harry'ANDpassword='5f4dcc3b5aa765d61d8327deb882cf99' |
| ' or '1'='1'# | blah | SELECT*FROMusersWHEREname='OR'1'='1'#' and password='6f1ed002ab5595859014ebf0951522d9' |
